“Read” or “View Only” Technology for the Insurance Industry

Brown & Meyer’s web-based dictation/transcription portal allows providers and their staff to process documents directly from their web account. However, we realize that some of our clients are not able to use web-based applications because of IT security concerns. If that is a concern for you, we are pleased to offer workflows that use read or view only data protection.
Not all systems and users need read or view-only protection for their documents, but for those that do, the need is usually triggered by a need to protect data from users, or by a need to protect a network from intrusion. In high-security environments where editing documents stored on a web-based application are not permitted we have alternative solutions to allow for successful workflows.
What is “Read” or “View only”?
The terms “read or view only” are defined as “In relation to memory, data, or a file, being able to be accessed but not modified.” While that sounds simple enough, the interpretation of the definition comes in different forms, and it’s important to understand the distinctions.
The key driver for how a “read or view only” function will be implemented is: what (or who) needs protection: the data, or the user? In other words, is it the data that needs to be protected from users, or, do users (or network systems) need to be protected from security risks? Let’s take a moment to explore each of the two scenarios common in a read or view-only approach to data protection.
Protecting data from users
When safeguards need to be implemented that protect data from users, the read or view-only access is seen in its most literal form. This type of read or view only occurs when data on a page cannot be accessed (other than viewed), copied, or “scraped” in any way by the user. An example of this would be an online banking access (see figure 1 below), where the copy/paste function is disabled, and the user has no way of moving data viewed on screen to a clipboard or file. The only access to the data is the user’s visual access, on screen.
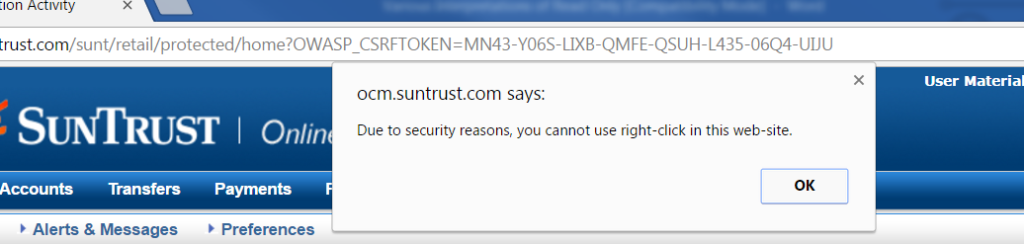
Figure 1: typical read-only access limitations on banking website.
An equivalent level of literal application of read or view only in document management is on-screen viewing of documents in an html form or image form, where the viewer has no means of copying or downloading the document. It’s not unlike a picture of the document, where the content is locked and untouchable, and never available for downloading.
Protecting users from data
Read or view-only access is also used in environments where users may have the authority to the data being accessed, but IT policies prohibit the installation of third-party software used to enable web-based documents from being edited via locally installed word processing software, which is the case with many of our large insurance company clients.
Web-based document management solutions are typically dependent on the installation of at least a small application to open and control the locally installed word processing software, and without that ability, document access can be accomplished only in a read or view-only mode. In that scenario, edits can be made, but only saved locally – not back to the original version of the document.
Maintaining an authoritative copy
When the user’s IT policies require document management via read or view-only access, it is sometimes important that a master copy of the document is retained and recognized as the authoritative version. For this we collect audit trail data as part of the process in maintaining the authentic version of the documents. We utilize two types of audit trailing:
1. Document history audit trail
Figure 2 (below) shows the document history audit trail on a transcribed document. Each row represents an earlier iteration of the document, which can be clicked to open. Editor access information is captured.
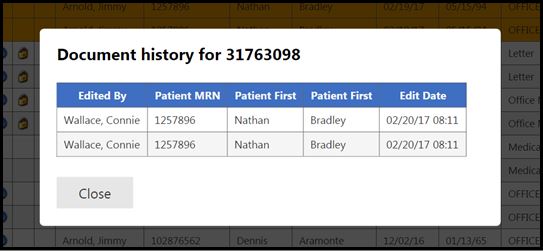
Figure 2: document history audit trail (patient information fictitious)
2. Full audit trail
Figure 3 (below) shows the full audit trail, which captures all document accesses, along with access information regarding the user and access date/time.
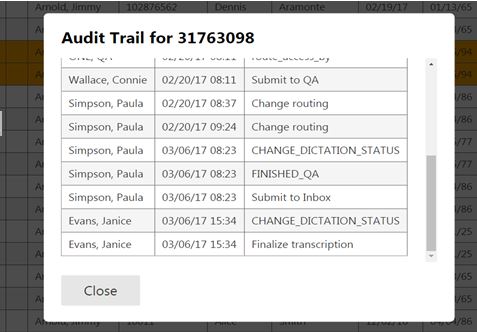
Figure 3: full audit trail (patient information fictitious)
Summary
Our web-based medical transcription platform meets the needs of our diverse client base, including:
- Private and group physician practices
- Multi-specialty clinics
- Hospital-based clinics
- Management companies
- Ambulatory Surgical Centers
- Small hospitals
We allow you to record your dictations 24 hours a day, 7 days a week, 365 days a year. After you dictate, you can expect to receive a complete transcript done by one of our fully trained medical transcriptionists within 24 hours.












